Keeping secrets is a pain - if more than one entity knows about it, it's not a secret anymore.
Quick problem description: I want to call my Web API using a Azure Logic App and I don't want the hassle of dealing with secrets and certificates.
This is where Azure Managed Identity usually comes in; this handy feature lets you assign an identity to your Logic App, VM, Web App - what have you - and then let Azure deal with the secrets and the rotation of such.
However, managed identity seems to be very geared towards Azure Resources such as Azure Key Vault, for instance.
When you create a managed identity, it does not show up as a user to which you can assign a role in your Azure Active Directory Enterprise Application.
You can follow these official docs to accomplish the same, but for me it's a bit of a long way around as you have to retrieve a bunch of object id's and such - also, I'd like this to be part of the Azure CLI.
So, I made my own Azure CLI extension which can be installed as easily as this:
az extension add --source https://www.frodehus.dev/dist/approle-0.1.0-py2.py3-none-any.whl
az approle assignment --help
Group
az approle assignment : Commands to manage assignment of app roles for service principals.
Command group 'approle' is in preview and under development. Reference and support
levels: https://aka.ms/CLI_refstatus
Commands:
add : Assign an app role to a service principal.
list : List all app role assignments for service principal.
remove : Remove an app role from a service principal.
Prepare your Azure Active Directory application
We need to have app roles defined and a Application URI (which will be the audience of our API and used to request tokens).
Once you have your application created, you need to set an Application URI.
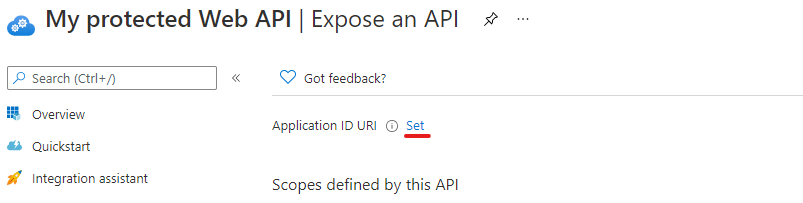
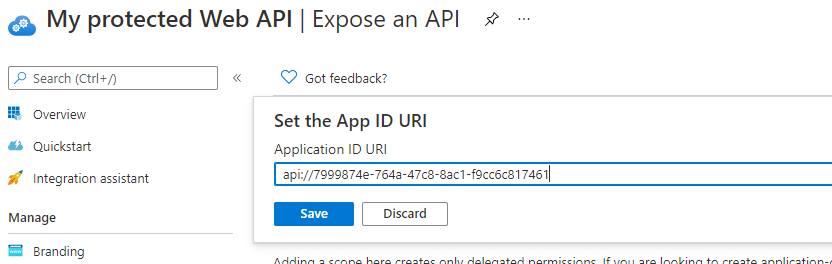
Click on Set and give it a name - the default is api://<guid> and will be autogenerated for you.
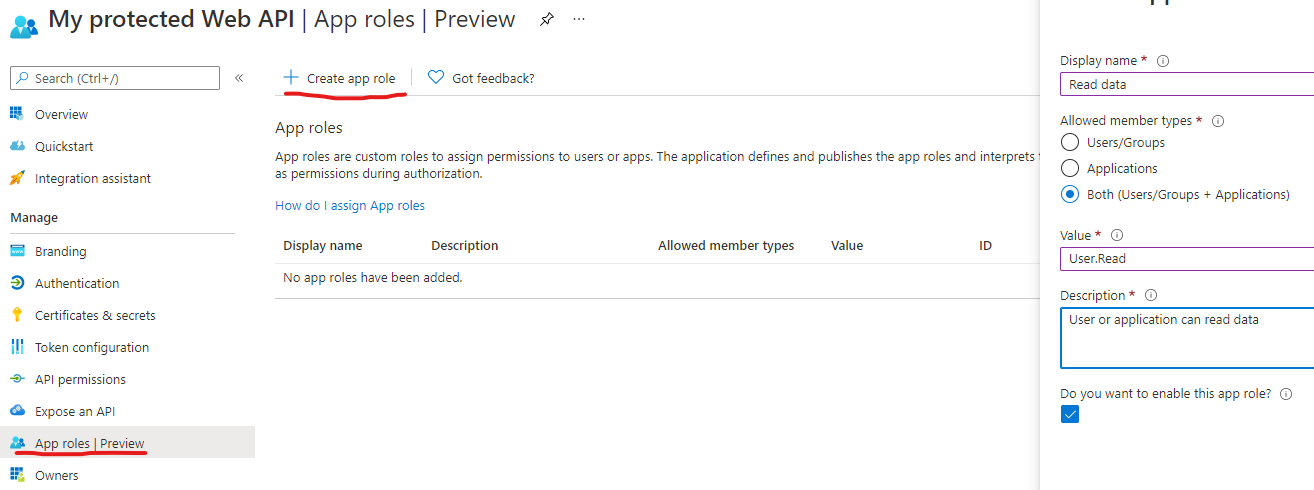
Next, we need app roles. You can create these with the new App roles preview blade in the portal.
We should now be ready to assign roles to our Azure Logic App!
Accessing your API from a Azure Logic App
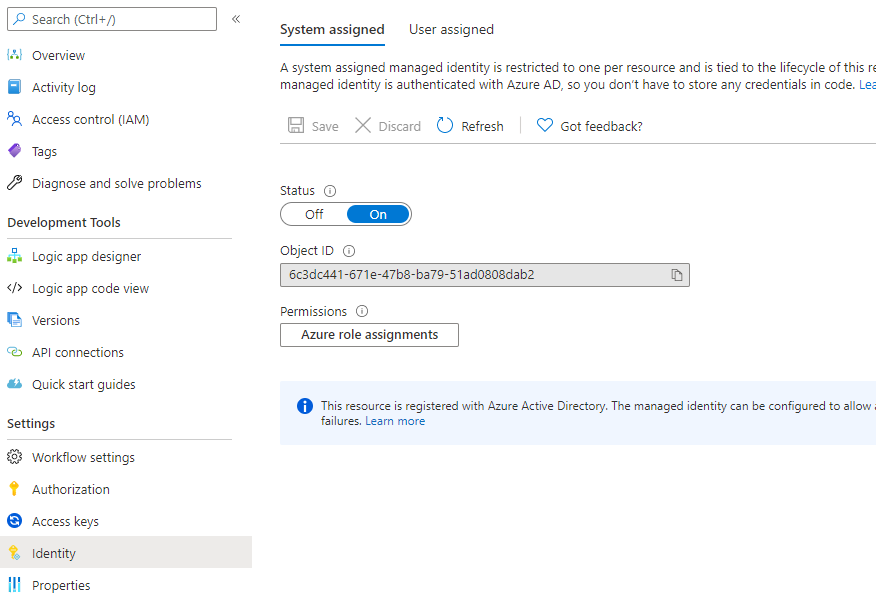
Before you can assign an app role, your logic app needs to have a managed identity.
Click on Identity and then toggle Status to On
Now you can assign the app role by using the name of the logic app, name of the Azure AD application and the value of the app role:
az approle assignment --service-principal "my logic app name" --app "My protected Web API" --role User.Read
Once the app role assignment is in place, you can use your Application URI (like you set above) to request a token and your newly assigned roles will be granted to you.
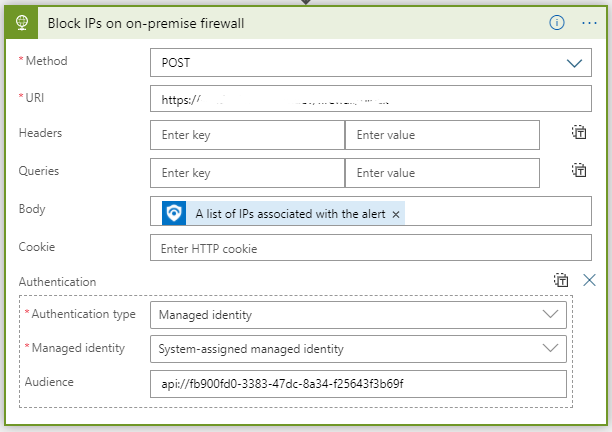
Now I can call my Azure AD protected Web API with app role without having to deal with secrets or certificates.

.jpg)